Theft in the cryptocurrency environment
We usually associate the cryptocurrency environment with advanced security measures to secure financial resources. There are even companies that offer cryptocurrency holders advanced methods of securing their wealth through military technology. Nevertheless, the problem of theft is not a foreign topic in the cryptocurrency community.
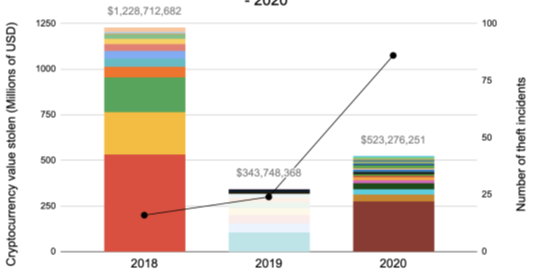
The graph above shows the size of cryptocurrency theft over a period of 3 years. Different colors indicate different cases of cryptocurrency theft, while the black line shows the number of recorded incidents.
Almost all cases of cryptocurrency theft fall into one of the three theft categories. The categories mentioned are: Exchange attacks, attacks on individuals, DeFi exploits.
Exchange attacks
At this point, thieves have stolen billions of dollars worth of cryptocurrency by attacking exchange wallets. Many companies, including such large and respected companies as Bitpoint, Binance, DragonEx, have been the subject of keen interest from hackers. The question arises as to how hackers managed to break through such advanced security. One of the most common methods used by hackers is social engineering. A hacker typically tries to trick employees of a particular cryptocurrency security company’s customers into downloading special malware that will give them access to one or more accounts. If the attacker is sufficiently determined, he will wait for months or even longer, observing patterns of money inflows and outflows so that he can sense the right moment to steal as much money as possible. What does this look like in practice? In one particularly audacious case, hackers set up a fake company, complete with website, social media presence and executive resumes. On the fake website, the hackers posted that they had created an automated trading bot and sent out several messages to employees of the companies/exchanges asking them to download and try a free trial version. At least one of the recipients was tempted by the offer. As it later turned out, the “free trial” included malware that helped hackers obtain the keys to private cryptocurrency wallets of several users. Immediately after gaining access to these accounts, the hackers began siphoning funds from these wallets. Hacking activity is a major threat for exchanges.
Attacks on individuals
A more common method of theft than widespread exchange attacks are attacks on individual cryptocurrency holders, which are also mainly carried out through phishing or social engineering. Any available figures showing the size of this method are unreliable as many people do not report their cryptocurrency stolen. A phishing attack targeting the company “Ledger” was launched in 2020. The company “Ledger” is a popular provider of physical devices on which to store cryptocurrency. In July 2020, the company revealed that the email addresses of many users had been compromised in a data security breach. A few months later in October, Ledger customers reported receiving emails from a perfectly fake website, imitating the real “Ledger” company website.
The fake email, informed Ledger customers that their servers had been hacked with malware and that customer funds were at risk. The email further advised that in order to protect against theft, it was necessary to click on a link that was in the email. By clicking on the link, customers were supposed to download the latest version of Ledger’s software. Once they followed the link, a website appeared that perfectly mimicked Ledger’s website. However, the email and website were part of a sophisticated phishing attack. Instead of downloading an update to the software, Ledger users who clicked the link in the fake email downloaded malware that emptied their virtual wallet. Overall, the CoinTelegraph website reported that Ledger customers who downloaded the malware lost a total of 1.1 million XRP (approximately $645,000) in just the first week after the hackers launched their campaign. Finally, at the end of 2020, in the Key players in crypto report by Chainalysis, we learn that a total of over $3.5 million worth of cryptocurrency was stolen.
DeFi Exploits
In 2020, DeFi platforms experienced a fairly large increase in users using them. Unfortunately, along with the increase in interest, went an increase in hacking attacks. Although DeFi represents only 6% of all cryptocurrency activity, DeFi platforms lost over 33% of their cryptocurrency holdings and fell victim to half of all hacking attacks. Overall, cybercriminals stole over $170 million worth of cryptocurrency from DeFi by means of price manipulation.
This manipulation was the key to almost every significant attack on DeFi platforms in 2020. Due to the fact that transactions on DeFi take place almost instantaneously with very few mechanisms in place to prevent suspicious transactions. Therefore, any thieves can reap huge profits by manipulating cryptocurrency prices on one or more DeFi platforms. These platforms rely heavily on tools called price oracles to obtain asset valuation data from an external source in order to ensure that the said assets are valued in line with the rest of the market. Most DeFi platforms use centralised price oracles that rely on only one node to send data to the rest of the platform and often use a single source of pricing data, thus exposing themselves to attack.
At first glance, price manipulation may seem like an ineffective method of attack for cybercriminals, as raising the price of any crypto asset requires upfront capital. However, this works differently at DeFi, thanks to flash loans.
Flash loans allow DeFi users to enjoy a variety of benefits, such as: receiving loans instantly without posting collateral; using borrowed funds to make transactions elsewhere; and repaying the loan in one instant transaction. If these users do not repay the loan, the entire transaction is immediately reversed, meaning that the lender receives the original capital back as if the loan had never taken place. In effect, this means little or no risk for both parties. It also means that lenders can charge very low interest rates on flash loans. Traders often use flash loans to raise the funds needed to take advantage of arbitrage opportunities and thus use the borrowed funds to take advantage of price discrepancies between platforms, ultimately ending up with a small profit after the loan is repaid.
Examples
Nevertheless, in 2020, cybercriminals took advantage of flash loans. They used the borrowed funds to buy crypto assets, raise the price and sell at a high profit. In this way, they easily repaid the loan and raked in the remaining funds. This is exemplified by two hacking attacks that occurred in February 2020 against the so-called bZx, or DeFi protocol, which allows users to build applications for decentralised lending, margin trading and other financial activities. The first time, cybercriminals borrowed a large amount of a cryptocurrency called Ether from bZx as a flash loan, used it to buy and drive up the price of packaged Bitcoin on Uniswap – at one point, the packaged Bitcoin price on Uniswap reached 109.8 ETH, compared to 38 for the overall market. The hackers then exchanged the packaged bitcoins for pure profit in the form of Ether, some of which was used to repay the original flash loan. In total, the attacker netted $350,000 in Ether cryptocurrency. The second attack, is a copy of the first and made a profit of $633,000.
An example of this type of theft from 2021 is more spectacular. On 10 August 2021, DeFi’s platform “Poly Network” announced that it had fallen victim to a hacking attack and lost $600 million. The stolen assets included about $253m in tokens on the Binance Smart Chain, $266m in Ethereum tokens and $85m in USDCs on the Polygon network, according to cryptocurrency wallet addresses revealed by Poly.
Experts say the hacker was able to exploit a cryptography or network coding issue. To authorise the movement of funds, users sign using cryptographic signatures or a string of letters and numbers similar to a password. In this case, the hacker likely targeted a weakness in the cryptography that allowed him to sign for the transfer of assets.
Despite the technological progress and thus the increase in anti-hacking safeguards, thefts targeting cryptocurrency holders will only increase, because with the increase in safeguards, the methods of theft will develop.
Sources:
https://www.cnbc.com/2021/08/11/over-600-million-dollars-was-stolen-in-a-massive-defi-hack.html
https://markets.chainalysis.com/ Chainalysis “Who is who in the Blockchain. Mapping the key players in the cryptocurrency ecosystem”
