KIEŁTYKA GŁADKOWSKI KG LEGAL constantly supervises and prepares its lawyers for the specialization in which they provide services for foreign clients. In order to systematize the conceptual grid of very specialized fields of IT, telecommunications, biology, medicine and modern finance, KIEŁTYKA GŁADKOWSKI conducts internal consultations to improve the experience of our lawyers specializing in legal assistance for foreign clients from the IT and TECH sector. As a result of such internal research, KIEŁTYKA GŁADKOWSKI creates and publishes texts on topics related to modern legal problems, but also to explain the basic concepts of specialized IT and pharmaceutical fields. In this way, KIEŁTYKA GŁADKOWSKI aims to demonstrate to potential clients within specialized industries that our lawyers are also familiar with specialist terms necessary for a proper understanding of our foreign client’s business and legal needs.
This is one of those texts. We invite you to read
it.
How to get a
cryptocurrency?
Cryptocurrency is
not emitted by some central, national bank as it happens with classical form of
money (fiat money). Cryptocurrency is made in a digital sphere and the only way
to obtain the currency from the blockchain system is to mine it (similarly and
metaphorically to the gold mining). Cryptocurrency mining works similarly to
the gold mining. Virtual coins can be discovered digitally using computer
programs. The Bitcoin, for instance, has set a limit of total of 21 million
bitcoins. Thus the faster you dig bitcoins the more of them you will have (if
we consider only mining). All bitcoins are lying within the blockchains system
and the role of the computer program and the miners is to dig it from that
system, precisely to discover it in that system. Thereby there can be one miner
or a clubbed miners’ group who dig together, faster and more effectively and
then they divide their profits among each other.
What is a mining
pool?
More
We usually associate the cryptocurrency
environment with advanced security measures to secure financial resources.
There are even companies that offer cryptocurrency holders advanced methods of
securing their wealth through military technology. Nevertheless, the problem of
theft is not a foreign topic in the cryptocurrency community.
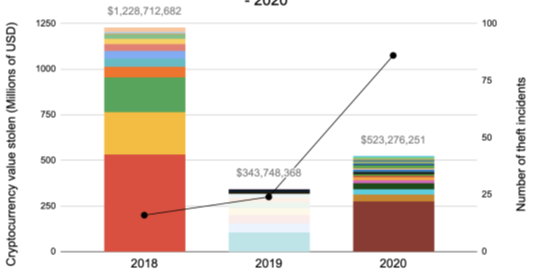
The graph above shows the size of
cryptocurrency theft over a period of 3 years. Different colors indicate
different cases of cryptocurrency theft, while the black line shows the number
of recorded incidents.
Almost all cases of cryptocurrency theft
fall into one of the three theft categories. The categories mentioned are:
Exchange attacks, attacks on individuals, DeFi exploits.
Exchange attacks
At this point, thieves have stolen
billions of dollars worth of cryptocurrency by attacking exchange wallets. Many
companies, including such large and respected companies as Bitpoint, Binance,
DragonEx, have been the subject of keen interest from hackers. The question
arises as to how hackers managed to break through such advanced security. One
of the most common methods used by hackers is social engineering. A hacker
typically tries to trick employees of a particular cryptocurrency security company’s
customers into downloading special malware that will give them access to one or
more accounts. If the attacker is sufficiently determined, he will wait for
months or even longer, observing patterns of money inflows and outflows so that
he can sense the right moment to steal as much money as possible. What does
this look like in practice? In one
particularly audacious case, hackers set up a fake company, complete with
website, social media presence and executive resumes. On the fake website, the hackers posted that
they had created an automated trading bot and sent out several messages to
employees of the companies/exchanges asking them to download and try a free
trial version. At least one of the recipients was tempted by the offer. As it
later turned out, the “free trial” included malware that helped
hackers obtain the keys to private cryptocurrency wallets of several users.
Immediately after gaining access to these accounts, the hackers began siphoning
funds from these wallets. Hacking activity is a major threat for exchanges.
More